Token based authentication
In the modern digital era, the way web applications are designed and developed has come a long way compared to traditional web applications. Accessing applications or resources is no more limited to computers. Rather mobile devices are being used widely to access websites and resources. The resources are not necessarily private in nature – and modern-day applications even extend certain resources to be accessible by external entities.
And in all such scenarios, security is of utmost importance. The resources being shared with the requestors must ensure authentication and authorization are implemented correctly protecting resources from being attacked by malicious users.
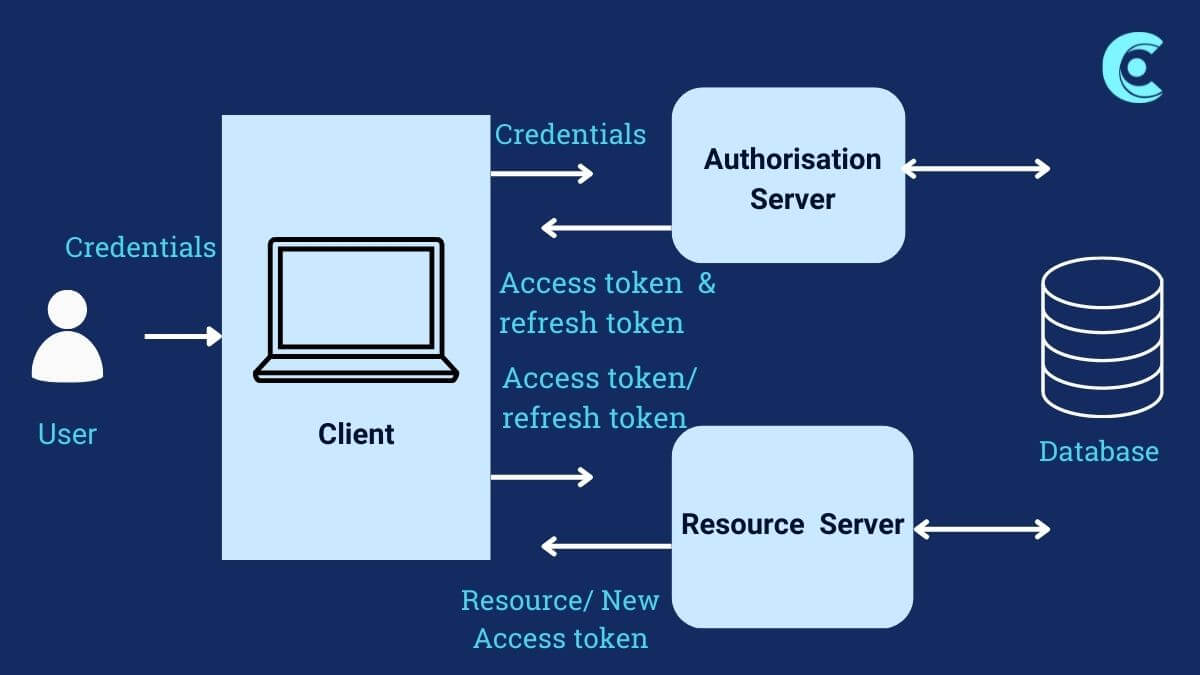
Token-based authentication provides a reliable and robust solution to ensure secure access to the resources within the network or beyond the private network boundaries. Based on the level of security, suitable options available – hardware tokens, software tokens, one-time passwords, biometric identities – can be selected. Usage of multi-factor authentication combined with tokens can create strong secure applications which are not easy to target by hackers/malicious users. Tokens not only offer better security but also enhance the user experience to transition thru multiple resources seamlessly – making the life of end users easier.
Token standards like OAuth/JWT are being widely adopted by developers due to ease of implementation along with a defined structure of the same in web applications/services. Tokens have inherent advantages like being stateless, having defined validity, and encrypted – authentication and authorization can be integrated within your application landscape easily. Technically – tokens like OAuth/JWT are typically stored on the client side without storing sensitive information on the same. This benefits the load balanced/fault tolerant environments to use resources like servers/applications with the same tokens – which otherwise would have meant centralized session management for servers in most of the traditional web applications.
With multiple customers, we have utilized OAuth tokens extensively for REST APIs. JWT was also used for cross-application integrations. If you are thinking of enhancing the security of your application landscape by consolidating the implementation of your authentication and authorization needs – utilizing tokens can be a good strategy to consider.
